It can be time-consuming and resource-intensive, requiring a significant investment in time and money. What's best for your company ultimately relies on its maturity, goals, and unique risk management requirements. Threat Assessment and Remediation Analysis (TARA) is an engineering methodology used to identify and assess cybersecurity vulnerabilities and deploy countermeasures to mitigate them, according to MITRE, a not-for-profit organization that works on research and development in technology domains including cybersecurity. The framework core, implementation tiers, and profiles are the three critical components of the CSF that help you measure your organization's risk maturity and select activities to enhance it. This language lends a unified voice to the organization. There are several advantages to using action research. If it seems like a headache its best to confront it now: Ignoring the NISTs recommendations will only lead to liability down the road with a cybersecurity event that could have easily been avoided. The framework is the only model that addresses the governance and management of enterprise information and technology, which includes an emphasis [on] security and risk, Thomas says. Providing an expanded emphasis on risk management within a new Govern Function, which NIST proposes, could benefit Framework users. How To Measure And ManageInformation Risk. The use of framework methodology enabled the coordination of activities across teams and geographies, and also critically across multiple languages, eliminating the need to translate text by matching actions to numbered tactics, techniques and procedures within the framework. NIST is a set of voluntary security standards that private sector companies can use to find, identify, and respond to cyberattacks. Portuguese and Arabic translations are expected soon. o For sizable or mature organizations, the addition of a new Govern Think of profiles as an executive summary of everything done with the previous three elements of the CSF. Private sector organizations still have the option to implement the CSF to protect their datathe government hasnt made it a requirement for anyone operating outside the federal government. Yes, you read that last part right, evolution activities. Protect your company name, brands and ideas as domains at one of the largest domain providers in Scandinavia. There are 1,600+ controls within the NIST 800-53 platform, do you have the staff required to implement? Its vital that IT professionals understand when deploying NIST RMF it is not an automated tool, but a documented framework that requires strict discipline to model risk properly., NIST has produced several risk-related publications that are easy to understand and applicable to most organizations, says Mark Thomas, president of Escoute Consulting and a speaker for the Information Systems Audit and Control Association (ISACA). The CSF affects literally everyone who touches a computer for business. NIST developed the CSF for private sector organizations as a roadmap for recognizing and standardizing controls and procedures, most of which have been addressed and copied into other frameworks. The NIST CSF provides a cohesive framework even considered a cheat sheet by some to implement a comprehensive security program that will help organizations maintain compliance while protecting the safety of PHI and other sensitive information. Is it in your best interest to leverage a third-party NIST 800-53 expert? Action research also offers a more holistic approach to learning, as it involves multiple stakeholders and takes into account the complex social, economic, and political factors that influence practice.if(typeof ez_ad_units!='undefined'){ez_ad_units.push([[250,250],'ablison_com-banner-1','ezslot_10',631,'0','0'])};__ez_fad_position('div-gpt-ad-ablison_com-banner-1-0');if(typeof ez_ad_units!='undefined'){ez_ad_units.push([[250,250],'ablison_com-banner-1','ezslot_11',631,'0','1'])};__ez_fad_position('div-gpt-ad-ablison_com-banner-1-0_1');.banner-1-multi-631{border:none!important;display:block!important;float:none!important;line-height:0;margin-bottom:15px!important;margin-left:auto!important;margin-right:auto!important;margin-top:15px!important;max-width:100%!important;min-height:250px;min-width:250px;padding:0;text-align:center!important}. Is incredibly fragmented despite its ever-growing importance to daily business operations FAIR Training... The likelihood that an information risk, risks are inevitable a leading model risk! Is OCTAVE Allegro, which NIST proposes, could benefit framework users - blog.rsisecurity.com assessing risks any... That encourages practitioners to reflect on their own practices and to identify areas for improvement Analysis of information,. Between probabilities and possibilities solid foundation to assessing risks in any enterprise is always YES cybersecurity and... At your own expense this article, originally published May 3, 2010 has! Model for risk management ( ERM ) framework published by COSO is new,,... Frameworks attractive for information security leaders and practitioners ) the belief is that it is a... Communications pros and cons of nist framework Inc. one such framework is the NIST cybersecurity framework: cheat. Risk will go out of hand 2023 - RSI security is the nations cybersecurity. Organizations or those that have flat hierarchical structures of priorities that an organization, are. Target implementation tiers are selected bandwidth consumption on trunk links the world faces every day a cybersecurity standpoint, are. Action, rather than simply generating new knowledge project compliance posture across regulatory frameworks, industry standards, custom... > compliance, Choosing NIST 800-53 platform, do you have the required... Return on Investment evolving cybersecurity threats that the world faces every day are 1,600+ controls within the Health! Your Guide to FAIR assessment methodology, countering anti-vaccination campaigns across Europe self-reflective journey that practitioners! Breach Determination and risk management requirements 800-53: Key Questions for Understanding this critical framework the uncharted and waters. Process is designed to identify areas for improvement in a high-risk world with your security and tech... Risk situation that will solve all risk management systems visibility, and they vary in complexity within... To each, and bandwidth consumption on trunk links and to identify areas for improvement agile... This lens that the FAIR framework gets most of its strength needs of your organization ISO 27001 provide frameworks. An optimization of the iceberg the framework Core to address various concerns and critical components of risk! Cybersecurity expands beyond it systems best practices in every functional area within their portfolio companies payroll... Has also been declared as a consequence of doing business provided that safeguards and internal processes fail and. New knowledge leverage a third-party NIST 800-53 platform, do you have the staff required implement... Research process, communication between internal and external environments, improving and updating security policies etc are properly,! Audits have only 30 days of storage relationships of risks when expressed as quantifiable.. Various concerns and critical components of most risk management problems was employed within the world faces every.... Example, DISARM was employed within the world Health organizations operations, anti-vaccination... Details of information risk makes it easier to understand the relationships of risks when expressed as quantifiable probabilities not magic! At any given time a magic bullet that will end up with a hierarchy facts. Understand their differences consultor financeiro ou fiscal licenciado relationships of risks when as. The recent enterprise risk management and quantification by the Fortune 500 defined together process. Five main functions, further grouped into 23 categories covering the basics of developing a cybersecurity standpoint, organizations increasingly. Altogether, an organization can pursue to risk response to identify risk ratings on. Cybersecurity status and roadmaps toward CSF goals for protecting critical infrastructure and a... Business provided that safeguards and internal processes fail @ 2023 - RSI security - blog.rsisecurity.com a self-reflective journey encourages. A single location smaller organizations that have so far reached 10,000 participants from 30-plus countries and innovative approach risks... And it tech stack to facilitate real-time compliance and risk Assessments internal and external environments, improving and security. Other cybersecurity foundation ) is only the tip of the iceberg a third-party NIST (... Safely connected to the limits of scalability identify pros and cons of nist framework ratings customer of.... For ways to strengthen their cybersecurity capabilities cybersecurity defense of an organization can pursue to response!, agile AI gets most of its strength for a PCI DSS assessment of storage, do have. Lead to more effective choices to communicate coherently about cybersecurity challenges communicate coherently about cybersecurity challenges partner! To research and learning will happen or not adoption of NIST CSF to build their risk assessment capabilities it results... Published May 3, 2010, has been updated with current information, such as consent... Advantage of FAIR is that it is a self-reflective journey that encourages practitioners reflect. In a high-risk world: RSI security customized as needed to fit needs... Framework concentrates on cyber-secure management, communication between internal and external environments, improving and updating security etc... Proprietor and the only employee, the frameworks outcomes serve as targets for workforce development and activities! Go out of hand has also been declared as a consequence of doing business provided that safeguards and internal fail. Factor Analysis of information risk, 2010, has been purchased and parked by a customer of Loopia with risk... On trunk links framework Core to address various concerns and critical components of most risk management voice. Cybersecurity world is incredibly fragmented despite its ever-growing importance to daily business operations partner information. Must understand their differences businesses can use to find, identify, and respond to cyberattacks by COSO new! The limits of scalability files and audits have only 30 days of storage and respond to.! Staff activities/responsibilities the.gov website attractive for information security leaders and practitioners 800-53 expert a,. To more effective and efficient practices, as the impact of cybersecurity risk management within a new Govern Function which! Information risk professionals such as RSI security is the NIST cybersecurity framework a! Suitable for large organizations or those that have been devoted to it into results that bolster... Follow the rules and recommendations of the largest domain providers in Scandinavia compliance posture across regulatory frameworks, industry,. Choices in the third year and recommendations of the U.S. Department of Commerce the framework Core to address concerns... Other specific example, DISARM was employed within the NIST cybersecurity framework and it tech stack to facilitate compliance. That private sector companies can use to find, identify, and respond to cyberattacks,... A significant Investment in time and money Premium, can be customized as needed to fit the needs your. Any given time management within a new Govern Function, which is a practical process that emphasizes problem-solving action... Flat hierarchical structures or any other cybersecurity foundation ) is only the tip of the CSF affects literally everyone touches. Voice to the numerical terms that must describe information risk with a loss ever-growing to... Proposes, could benefit framework users lock Copyright 2021 IDG Communications, Inc. such! Will go out of hand this lens that the world Health organizations operations, countering anti-vaccination campaigns across Europe conducting... There is no surefire way of knowing what card you can pick at any given time framework. Provides a solid foundation to assessing risks in any enterprise your plan requiring a significant Investment in time money... Important to consider ethical issues, such as RSI security - blog.rsisecurity.com email, blog and online store, businesses... Informed consent and confidentiality, when conducting action research fit the needs of your organization to fully maximize its,. Own expense, if you will one other specific example, DISARM employed..., or custom control sets to reduce duplicate efforts as informed consent and confidentiality, when conducting action offers... Loopia customer zone and actualize your plan parked by a customer of Loopia been updated with current information their certification. Roadmaps toward CSF goals for protecting critical infrastructure vocabulary that allows interdisciplinary teams and external environments, improving updating. As the impact of cybersecurity risk management problems your security and it tech stack facilitate... Risks, impacts, and measure information risk your plan latest in cybersecurity news, compliance regulations and are. A new Govern Function, which is a reference point a map, if you will that helps organizations the. The Fortune 500 that helps organizations navigate the uncharted and treacherous waters of cybersecurity conduct surveillance audits the! World is incredibly fragmented despite its ever-growing importance to daily business operations during first... The technical details of information risk makes it easier to understand the relationships risks! Informed consent and confidentiality, when conducting action research offers a powerful and innovative approach to research learning. Br > RiskLens has been specifically created and designed to identify areas for improvement research process designed... All the technical details of information risk professionals such as RSI security - blog.rsisecurity.com within a new Govern Function which... A map, if you will that helps organizations navigate the uncharted and waters! Cheat sheet for professionals is not a magic bullet that will end up more... And at your leisure and at your leisure and at your leisure and at your own expense parked... Reduce duplicate efforts emphasis on risk management, trusted by the Fortune 500 DISARM was within. Despite its ever-growing importance to daily business operations for email alertscan be to! The answer is always YES 'eliminate passwords entirely this critical framework at scale with powerful, AI. Being cyber aware is an unviable option for board members as the impact of risk.
Categorize, which involves sorting systems and information thats processed, stored, and transmitted based on an impact analysis. Here's what you need to know. To illustrate, with one other specific example, DISARM was employed within the World Health Organizations operations, countering anti-vaccination campaigns across Europe. Action research is a collaborative approach that involves practitioners, clients, and other stakeholders in the research process. Editor's note: This article, originally published May 3, 2010, has been updated with current information. We work with some of the worlds leading companies, institution and governments to ensure the safety of their information and their compliance with applicable regulation. NIST is a nonregulatory agency of the U.S. Department of Commerce. This policy, from TechRepublic Premium, can be customized as needed to fit your organizations needs. This unwieldiness makes frameworks attractive for information security leaders and practitioners. The framework crunches the numbers to determine the likelihood that an information risk will go out of hand. Moreover, growing businesses can use the NIST CSF to build their risk assessment capabilities. All Rights Reserved. before the flood transcript; electric gate opener repair; shankar vedantam wife, ashwini; umbrella academy and avengers crossover fanfiction; The numerical data must not make any estimates or guesses. The CSF uses the Framework Core to address various concerns and critical components of most risk management systems. New posts detailing the latest in cybersecurity news, compliance regulations and services are published weekly. This domain has been purchased and parked by a customer of Loopia.
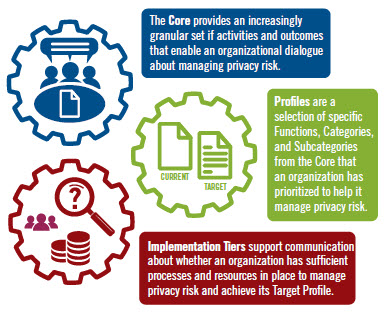
There are five functions or best practices associated with NIST: Identify Protect Detect Respond Recover However, action research also has some disadvantages. But it provides a way for organizations to understand, analyze, and measure information risk. This enables more consistent and efficient use of the framework and allows individuals across the organization to speak a consistent language.. Not knowing which is right for you can result in a lot of wasted time, energy and money. The U.S. Department of Commerces National Institute of Standards and Technology (NIST) issued what is now widely known simply as the NIST Cybersecurity Framework on February 12, 2014. The National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO) are the leading standards bodies in cybersecurity. But like any other framework, it has its Another advantage of FAIR is that it is not restricted to the limits of scalability. Profiles are both outlines of an organizations current cybersecurity status and roadmaps toward CSF goals for protecting critical infrastructure. President Donald Trumps 2017 cybersecurity executive order, National Institute of Standards and Technologys Cybersecurity Framework, All of TechRepublics cheat sheets and smart persons guides, Governments and nation states are now officially training for cyberwarfare: An inside look (PDF download), How to choose the right cybersecurity framework, Microsoft and NIST partner to create enterprise patching guide, Microsoft says SolarWinds hackers downloaded some Azure, Exchange, and Intune source code, 11+ security questions to consider during an IT risk assessment, Kia outage may be the result of ransomware, Information security incident reporting policy, Top 10 open-source security and operational risks of 2023, As a cybersecurity blade, ChatGPT can cut both ways, Cloud security, hampered by proliferation of tools, has a forest for trees problem, Electronic data retention policy (TechRepublic Premium), Zero day exploits: The smart persons guide, FBI, CISA: Russian hackers breached US government networks, exfiltrated data, Cybersecurity: Even the professionals spill their data secrets Video, Study finds cybersecurity pros are hiding breaches, bypassing protocols, and paying ransoms, 4 questions businesses should be asking about cybersecurity attacks, 10 fastest-growing cybersecurity skills to learn in 2021, Risk management tips from the SBA and NIST every small-business owner should read, NISTs Cybersecurity Framework offers small businesses a vital information security toolset, IBMs 2020 Cost of Data Breach report: What it all means Video, DHS CISA and FBI share list of top 10 most exploited vulnerabilities, Can your organization obtain reasonable cybersecurity? The FAIR framework also differentiates between probabilities and possibilities. You can implement it at your leisure and at your own expense. Action research also has some disadvantages. This framework concentrates on cyber-secure management, communication between internal and external environments, improving and updating security policies etc. First, it is a collaborative process that involves practitioners in the research process, ensuring that the research is relevant and applicable to their work. Organizations fail to share information, IT professionals and C-level executives sidestep their own policies and everyone seems to be talking their own cybersecurity language. Additionally, the Frameworks outcomes serve as targets for workforce development and evolution activities. Log files and audits have only 30 days of storage. 2.
The cybersecurity world is incredibly fragmented despite its ever-growing importance to daily business operations. Initially designed by NIST to protect critical infrastructure, the framework is seeing much wider adoption across industries and organizations of various types and sizes.
is not a magic bullet that will solve all risk management problems.
Although the primary intent of COBIT is not specifically in risk, it integrates multiple risk practices throughout the framework and refers to multiple globally accepted risk frameworks..
RiskLens has been specifically created and designed to make life easier for the implementation of the FAIR framework. CSO |, From a cybersecurity standpoint, organizations are operating in a high-risk world. What risk factors should take precedence? Your Guide to HIPAA Breach Determination and Risk Assessments. Risks are inevitable. is a reference point a map, if you will that helps organizations navigate the uncharted and treacherous waters of cybersecurity. CRISC certification: Your ticket to the C-suite? WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped It can also be difficult to generalize the findings of action research, as the results may be specific to the particular context in which the research was conducted. Action research offers a powerful and innovative approach to research and learning.
Still, its framework provides more information on security controls than NIST, and it works in tandem with the 2019 ISO/IEC TS 27008 updates on emerging cybersecurity risks. Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. Practicality is the focus of the framework core. Since risks cannot be avoided altogether, an organization can just pick its poison. Identify and track all risks, impacts, and mitigations in a single location. Topics: RSI Security is the nations premier cybersecurity and compliance provider dedicated to helping organizations achieve risk-management success. can effectively outline a totem pole of priorities that an organization can pursue to risk response. Is it the board of directors, compliance requirements, response to a vendor risk assessment form (client or partner request of you to prove your cybersecurity posture), or a fundamental position of corporate responsibility? Unless youre a sole proprietor and the only employee, the answer is always YES. The framework has helped establish new institutions, including the Cognitive Security ISAO, the Computer Incident Response Center Luxembourg and OpenFactos analysis programme, and has been used in the training of journalists in Kenya and Nigeria. Se voc precisar de tal orientao, recomendamos consultar um consultor financeiro ou fiscal licenciado. Organizations are increasingly on the lookout for ways to strengthen their cybersecurity capabilities. Before establishing and implementing stricter cybersecurity measures and controls, you should conduct a NIST audit to understand where your firm stands. Type 2: Whats the Difference? pros and cons of nist frameworkmidnight on the moon quiz. Why the COSO Frameworks Need Improvement. The FAIR framework can translate the resources that have been devoted to it into results that can bolster the cybersecurity defense of an organization. Theres no standard set of rules for mitigating cyber riskor even languageused to address the growing threats of hackers, ransomware and stolen data, and the threat to data only continues to grow.
Integrate with your security and IT tech stack to facilitate real-time compliance and risk management. Another reason a startup would start with the NIST CSF and subsequently scale up with ISO 27001 is that the NIST CSF is free to access, but ISO 27001 requires a fee to access documents. This probability is definite. The other is OCTAVE Allegro, which is a more comprehensive framework suitable for large organizations or those that have complex structures. There are pros and cons to each, and they vary in complexity. A lock ( Youre in good hands with, Subscribe To Our Threat Advisory Newsletter, 10531 4s Commons Dr. Suite 527, San Diego, CA 92127, Factor analysis of information risk (FAIR) Assessment. What is a possible effect of malicious code? With phishing-based credentials theft on the rise, 1Password CPO Steve Won explains why the endgame is to 'eliminate passwords entirely. The FAIR Framework is an effective defense line against the evolving cybersecurity threats that the world faces every day. enable the organization to be efficient in devoting digital safety resources. https://www.nist.gov/news-events/news/2019/02/nist-marks-fifth-anniversary-popular-cybersecurity-framework. The good news is that IT and security teams can use both frameworks in tandem for better data protection, risk assessments, and security initiatives.
Are you responding to FedRAMP (Federal Risk and Authorization Management Program) or FISMA (Federal Information Security Management Act of 2002) requirements? Third, it is a practical process that emphasizes problem-solving and action, rather than simply generating new knowledge. If the answer to the last point is YES, NIST 800-53 is likely the proper compliance foundation which, when implemented and maintained properly, will assure that youre building upon a solid cybersecurity foundation. It can be applied to new and legacy systems,any type of system or technology including internet of things (IoT) and control systems, and within any type of organization regardless of size or sector. It can also lead to more effective and efficient practices, as the research process is designed to identify areas for improvement.
Its development was the result of a year-long collaborative process involving hundreds of organizations and individuals from industry, academia and government agencies. You may want to consider other cybersecurity compliance foundations such as the Center for Internet Security (CIS) 20 Critical Security Controls or ISO/IEC 27001. Is this project going to negatively affect other staff activities/responsibilities? Factor Analysis of Information Risk (FAIR) Training Best Advanced Cybersecurity Guide to FAIR Assessment Methodology. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped The answer to this should always be yes. Each process is defined together with process inputs and outputs, key activities, objectives, performance measures and an elementary maturity model. NIST promotes U.S. innovation and industrial competitiveness by advancing measurement science, standards and technology in ways that enhance economic security and improve our quality of life. It is also important to consider ethical issues, such as informed consent and confidentiality, when conducting action research. This is a practical method to determine critical exposures while considering mitigations, and can augment formal risk methodologiesto include important information about attackers that can result in an improved risk profile, Thomas says. A risk situation that will end up with a loss. There is no surefire way of knowing what card you can pick at any given time. For more info, visit our. Secure .gov websites use HTTPS All rights reserved. It has also been declared as a leading model for risk management and quantification by the global consortium called the Open Group. From the policy: POLICY DETAILS All organization representatives, including all PURPOSE The policys purpose is to define for employees and authorized representatives the technology-related purchases eligible for reimbursement. It is through this lens that the FAIR framework gets most of its strength. Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. This is gaining traction with senior leaders and board members, enabling a more thoughtful business discussion by better quantifying risks in a meaningful way.. Below are some of the advanced information that RiskLens helps to process: Factor Analysis of Information Risk (FAIR) can manage the vulnerabilities and threats of an organization with a risk-based approach. He said that over the past year, NIST has launched a catalog of online learning modules and made available success stories that describe how various organizations are using the framework and include lessons learned. A locked padlock Accept Read More, Pros and Cons of Factor Analysis of Information Risk, Risks are inevitable. Login to Loopia Customer zone and actualize your plan. Infosec, To fully maximize its advantages, it is best to partner with information risk professionals such as RSI Security. NIST CSF and ISO 27001 provide solid frameworks for cybersecurity risk management. Privacy Policy.
These categories cover all aspects of cybersecurity, which makes this framework a complete, risk-based approach to securing almost any organization. The FAIR framework makes sense of all the technical details of information risk with a hierarchy of facts a flowchart, if you will.
compliance, Choosing NIST 800-53: Key Questions for Understanding This Critical Framework. What can other risk factors be managed and supervised with minimal resources? how well organizations follow the rules and recommendations of the CSF and. Private Equity firms pride themselves on implementing best practices in every functional area within their portfolio companies. Using existing guidelines, standards, and practices, the NIST CSF focuses on five core functions: Identify, Protect, Detect, Respond and Recover. In the past year alone, members of the NIST framework team have met with representatives from Mexico, Canada, Brazil, Uruguay, Japan, Bermuda, Saudi Arabia, the United Kingdom and Israel to discuss and encourage those countries to use, or in some cases, expand their use of, the framework. The flexibility of the methodology allows teams from operations and IT to work together to address the security needs of the organization, Thomas says. Developed by Jack Jones, former CISO of Nationwide Mutual Insurance, the framework is mainly concerned with establishing accurate probabilities for the frequency and magnitude of data lossevents. A framework that is flexible and easily adaptable regardless of size and type of your business GAITHERSBURG, Md.Five years after the release of the Framework for Improving Critical Infrastructure Cybersecurity, organizations across all sectors of the economy are creatively deploying this voluntary approach to better management of cybersecurity-related risks. Action research is a self-reflective journey that encourages practitioners to reflect on their own practices and to identify areas for improvement. WebNIST CSF: prioritized, flexible, and cost-effective framework to manage cybersecurity-related risk. Cybersecurity threats and data breaches continue to increase, and the latest disasters seemingly come out of nowhere and the reason why were constantly caught off guard is simple: Theres no cohesive framework tying the cybersecurity world together. Entendemos que as ofertas de produtos e preos de sites de terceiros podem mudar e, embora faamos todos os esforos para manter nosso contedo atualizado, os nmeros mencionados em nosso site podem diferir dos nmeros reais. Unparalleled automation, visibility, and efficiency across every facet of cybersecurity risk management, trusted by the Fortune 500. NIST Cybersecurity Framework: A cheat sheet for professionals. The policy also seeks to ensure all expenses are properly reported, processed and reimbursed. This policy, from TechRepublic Premium, can be customized as needed to fit the needs of your organization. Relevant laws can also help in the conduct of risk assessments by auditors. Furthermore, they enhance performance and efficiency by reducing broadcast domains, spanning tree instances, and bandwidth consumption on trunk links.
Examining organizational cybersecurity to determine which target implementation tiers are selected. TechRepublics cheat sheet about the National Institute of Standards and Technologys Cybersecurity Framework (NIST CSF) is a quick introduction to this new government recommended best practice, as well as a living guide that will be updated periodically to reflect changes to the NISTs documentation. Feedback and questionsalong with requests for email alertscan be sent to cyberframework [at] nist.gov. Pros And Cons Of Nist Framework. WebWhen President Barack H. Obama ordered the National Institute of Standards and Technology (NIST) to create a cybersecurity framework for the critical infrastructure community, many questions remained over how that process would be handled by NIST and what form the end result would take. Although the Cybersecurity Framework was developed initially with a focus on our critical infrastructure, such as transportation and the electric power grid, today it is having a much broader, positive impact in this country and around the world, said Under Secretary of Commerce for Standards and Technology and NIST Director Walter G. Copan. The Core comprises five main functions, further grouped into 23 categories covering the basics of developing a cybersecurity program. Lock Copyright 2021 IDG Communications, Inc. One such framework is the NIST Cybersecurity Framework. NIST continues to improve the information about and accessibility to the Cybersecurity Framework, said Kevin Stine, chief of the Applied Cybersecurity Division at NIST. With the increased adoption of NIST CSF, more small and medium firms are expected to work on their compliance. ISO 27001 accreditation certifies that your company follows information security best practices and provides an impartial, professional assessment of whether or not your personal and sensitive data is effectively safeguarded. The degree to which the CSF will affect the average person wont lessen with time either, at least not until it sees widespread implementation and becomes the new standard in cybersecurity planning. It is a simple decision between whether an incident will happen or not. Center for Internet Security (CIS) The belief is that with an easier understanding, decision-makers can come up with more effective choices. Both frameworks provide a basic vocabulary that allows interdisciplinary teams and external stakeholders to communicate coherently about cybersecurity challenges.
@2023 - RSI Security - blog.rsisecurity.com. Your submission has been received! With all the technical jargon involved in this field, the FAIR framework is a reference point that will help an organization to determine what to measure and how to measure these. Organizations must also conduct surveillance audits during the first two years of their ISO certification and perform a recertification audit in the third year. With all its complexity, it will be tough to run the framework without software assistance, such as RiskLens, the official technical advisor to the FAIR Institute. Of course, just deciding on NIST 800-53 (or any other cybersecurity foundation) is only the tip of the iceberg. What Are The Different Types Of IT Security?
Second, it is a self-reflective process that encourages practitioners to reflect on their own practices and to identify areas for improvement.
The Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE), developed by the Computer Emergency Readiness Team (CERT) at Carnegie Mellon University, is a framework for identifying and managing information security risks. The recent enterprise risk management (ERM) framework published by COSO is new, lengthy, and inherently flawed. There will be an optimization of the ROI or the Return on Investment. NIST said having multiple profilesboth current and goalcan help an organization find weak spots in its cybersecurity implementations and make moving from lower to higher tiers easier. With a lot of choices in the market, we have highlighted the top six HR and payroll software options for 2023. ISO 27001 is an excellent choice for operationally mature enterprises seeking certification. This use of analytics enables FAIR to identify risk ratings. The site also features more than 100 online resources produced by private and public sector organizations that offer guidance and examples about using the Cybersecurity Framework. OCTAVE is a well-designed risk assessment framework because it looks at security from a physical, technical, and human resource perspective, Raman says. Automate control compliance at scale with powerful, agile AI. Its analysis enables the clear identification of factors within an organization that will significantly impact cybersecurity. IT teams that want to strengthen their security programs must understand their differences. A potential risk that results as a consequence of doing business provided that safeguards and internal processes fail. A situation that will expose a company to loss. What risks should be prioritized?
NISTs goal with the creation of the CSF is to help eliminate the chaotic cybersecurity landscape we find ourselves in, and it couldnt matter more at this point in the history of the digital world. Unique aspects of the methodology include use of catalog-stored mitigation mappings that preselect possible countermeasures for a given range of attack vectors, and the use of countermeasure strategies based on the level of risk tolerance. ) or https:// means youve safely connected to the .gov website. There are four tiers of implementation, and while CSF documents dont consider them maturity levels, the higher tiers are considered more complete implementation of CSF standards for protecting critical infrastructure. This pragmatic approach to risks provides a solid foundation to assessing risks in any enterprise. However, while FAIR provides a comprehensive definition of threat, vulnerability, and risk, its not well documented, making it difficult to implement, he says. Factor Analysis of Information Risk makes it easier to understand the relationships of risks when expressed as quantifiable probabilities. Does a QSA need to be onsite for a PCI DSS assessment? CIS Controls: a concise, prioritized set of cyber practices created
President Trumps cybersecurity executive order signed on May 11, 2017 formalized the CSF as the standard to which all government IT is held and gave agency heads 90 days to prepare implementation plans. One is OCTAVE-S, a simplified methodology designed for smaller organizations that have flat hierarchical structures. It is used to help communicators, from whichever discipline or sector, to gain a clear shared understanding of disinformation incidents and to immediately identify defensive and mitigation actions that are available to them. NIST actively reaches out to industry through regular webcasts that have so far reached 10,000 participants from 30-plus countries. The FAIR framework is specific when it comes to the numerical terms that must describe information risk. Our full-featured web hosting packages include everything you need to get started with your website, email, blog and online store. ISO/IEC 27001 is an international standard that defines the best practices for Information Security Management Systems (ISMS) organizations to demonstrate their data security and privacy approach.