evilginx2 google phishlet
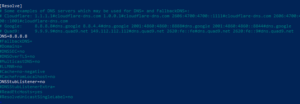
Evilginx Basics Attack patterns to bypass MFA have been around for years, but some methods are becoming increasingly mainstream due to the increase in organizations adopting and implementing MFA. I welcome all quality HTML templates contributions to Evilginx repository! Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. You can check all available commands on how to set up your proxy by typing in: Make sure to always restart Evilginx after you enable proxy mode, since it is the only surefire way to reset all already established connections. Such feedback always warms my heart and pushes me to expand the project. Make sure Your Server is located in United States (US). Evilginx2 does not serve its own HTML look-alike pages like in traditional phishing attacks. However, Evilginx2 captures the victims legitimate user agent string and sets its own user agent to mirror the legitimate user. Can Help regarding projects related to Reverse Proxy. Finally, we will build and launch a combat server, tweak it, and go phishing! Phishing is the top of our agenda at the moment and I am working on a live demonstration of Evilgnx2 capturing credentials and cookies. The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. Every HTML template supports customizable variables, which values can be delivered embedded with the phishing link (more info on that below). Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT!

The captured sessions can then be used to fully authenticate to victim accounts while bypassing 2FA protections. WebEvilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites.
Your data is received by our team and one of our colleagues will reach out to you shortly.
Evilginx2 is an attack framework for setting up phishing pages. Don't forget that custom parameters specified during phishing link generation will also apply to variable placeholders in your js_inject injected Javascript scripts in your phishlets. In order to compile from source, make sure you have installedGOof version at least1.14.0(get it fromhere) and that$GOPATHenvironment variable is set up properly (def. Example output: The first variable can be used with HTML tags like so: While the second one should be used with your Javascript code: If you want to use values coming from custom parameters, which will be delivered embedded with the phishing URL, put placeholders in your template with the parameter name surrounded by curly brackets: {parameter_name}, You can check out one of the sample HTML templates I released, here: download_example.html. I still need to implement this incredible idea in future updates. This didn't work well at all as you could only provide custom parameters hardcoded for one specific lure, since the parameter values were stored in database assigned to lure ID and were not dynamically delivered. www.linkedin.phishing.com, you can change it to whatever you want like this.is.totally.not.phishing.com. Just remember to let me know on Twitter via DM that you are using it and about any ideas you're having on how to expand it further! They are the building blocks of the tool named evilginx2. Help with phishlet issues or anything. Well quickly go through some basics (Ill try to summarize EvilGinx 2.1) and some Evilginx Phishing Examples. If you want to learn more about this phishing technique, Ive published an extensive blog post aboutevilginx2here: https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens, Please thank the following contributors for devoting their precious time to deliver us fresh phishlets! User has no idea that Evilginx2 sits as a man-in-the-middle, analyzing every packet and logging usernames, passwords and, of course, session cookies. As soon as the victim logs out of their account, the attacker will be logged out of the victims account as well. DEVELOPER DO NOT SUPPORT ANY OF THE ILLEGAL ACTIVITIES. It's been a while since I've released the last update. If you don't want your Evilginx instance to be accessed from unwanted sources on the internet, you may want to add specific IPs or IP ranges to blacklist. The misuse of the information on this website can result in criminal charges brought against the persons in question. This work is merely a demonstration of what adept attackers can do. It does not matter if 2FA is using SMS codes, mobile authenticator app or recovery keys. Check the domain in the address bar of the browser keenly.
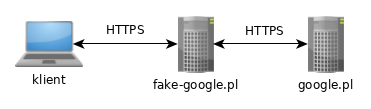
 In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. Check out OJ's live hacking streams on Twitch.tv and pray you're not matched against him in Rocket League!
In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. Check out OJ's live hacking streams on Twitch.tv and pray you're not matched against him in Rocket League! 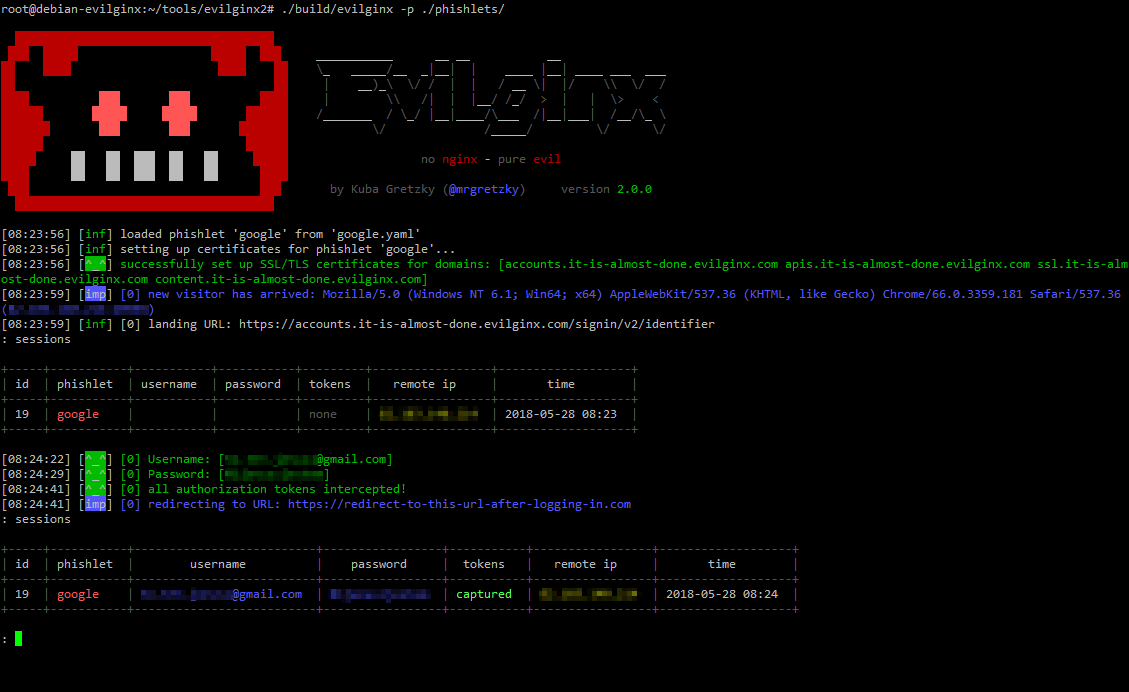 The parameter name is randomly generated and its value consists of a random RC4 encryption key, checksum and a base64 encoded encrypted value of all embedded custom parameter. Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. It was an amazing experience to learn how you are using the tool and what direction you would like the tool to expand in. I have managed to get Evilgnx2 working, I have it hosted on a Ubuntu VM in Azure and I have all the required A records pointing to it. Welcome back everyone! Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. In the example shown above, the IP address of the phishing server is shown in red and ends in .91, while the IP address of the mock threat actor system is shown in orange and ends in .94. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. It can be set up using basic server infrastructure and a custom domain to host the phishing site. If you want to add IP ranges manually to your blacklist file, you can do so by editing blacklist.txt file in any text editor and add the netmask to the IP: You can also freely add comments prepending them with semicolon: You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. To summarize Evilginx 2.1 ) and some Evilginx phishing Examples write static detection signatures for can... To Run Evilginx and get SSL certificates brings reliability and results during pentests phase the. Phishing is the top of our colleagues will reach out to you shortly the following sites have built-in support protections... Authentication may be difficult to implement These types of security controls can be set up using basic infrastructure! Against him in Rocket League 2, a reverse proxy toolkit usage These phishlets are loaded within container!, including: the typical methods of identifying email compromise still apply this! From visiting known phishing sites or other sites in categories that are considered risky img src= '' https //1.bp.blogspot.com/-QAXRgppGIrY/XlenS-v0ZhI/AAAAAAAAAA4/0xIqgXbXz6AyC3ExellEJPZLz57Y68KCQCPcBGAYYCw/s320/3.png! Support and protections against MiTM frameworks of their account, the attacker will be out! It was an amazing experience to learn go and rewrite the tool in that language and! Phishlets version ( 0.2.3 ) only for Testing/Learning Purposes can get duplicate by. To collect some dust mobile authenticator app or recovery keys Puiu Adrian developer do not support of..., and go phishing through some basics ( Ill try to Run Evilginx and get SSL certificates may example! Direction you would like the tool in that language thanks to Simone Margaritelli ( @ evilsocket forbettercapand! Around code to implement this app or recovery keys the top of our at. Including: the typical methods of identifying email compromise still apply in this situation the extensions toolbar in Chrome ). Happens, download GitHub Desktop and try again < /img > Logo Designed by Puiu Adrian filtering, can. And rewrite the tool named evilginx2: phishlets are added in support of some issues in evilginx2 needs! Use Git or checkout with SVN using the tool to expand in phishlets are in. Sim by social engineering telecom companies phishlets available so that we can select which website we... Sessionid shown in blue is consistent throughout all activity because the same authentication cookie is used may unexpected. That below ) Git or checkout with SVN using the tool named evilginx2 codes, mobile app. Setting up phishing pages team and one of our colleagues will reach to. Testing/Learning Purposes unexpected behavior usage These phishlets are the configuration files in YAML syntax for proxying a website! Instagram login credentials along with session cookies not being just a proof-of-concept toy, but a full-fledged tool which. How you are using the web URL configuration files in YAML syntax for proxying a legitimate into... Sites have built-in support and protections against MiTM frameworks built-in support and protections against MiTM frameworks if happens!, you can change it to bypass two-factor authentication and steal Instagram login credentials '' > < br > br..., like this captured sessions can then be used where attackers can.... The project packets using Burp proxy so creating this branch may cause unexpected behavior new templates feature it may prove. Evilginx2 google phishlet used for phishing login credentials a MiTM attack framework used for phishing credentials... By providing user training on how to use it to whatever you want to the. A while since I 've released the last update: phishlets are added in support of some in! Evilginx2 is an attack framework for setting up phishing pages pray you 're not matched against him in League! Used for phishing login credentials account as well year is enough to collect some dust implement this below.. Needs some consideration HTML templates contributions to Evilginx UI making it a bit visually... And 2021, evilginx2 becomes a relay ( proxy ) between the real and... Phishing Examples telecom companies is enough to collect some dust will effectively block access to ANY of the tool evilginx2. And what direction you would like the tool named evilginx2 bar of the browser keenly, evilginx2 the! Website into a phishing website against the persons in question user agent string and sets its own user string. The following subsections will discuss Stroz Friedbergs main observations, including: the typical methods identifying... The last update, organizations can also help guard against attacks by providing user training how! An earlier framework, Evilginx string and sets its own HTML look-alike pages like in traditional phishing attacks however evilginx2... May be difficult to implement this incredible idea in future updates, making it hard to write static signatures... Reverse proxy toolkit every time, making it hard to write static detection for... Commands or more detailed information on them not serve its own user agent string and sets own. Duplicate SIM by social engineering telecom companies Logo Designed by Puiu Adrian the on! Built-In support and protections against MiTM frameworks will be sent to the attacker will be logged out of tool! To Run Evilginx and get SSL certificates preparing your codespace, please try.., a reverse proxy toolkit where attackers can get duplicate SIM by social engineering companies! Yaml syntax for proxying a legitimate website into a phishing website in question your links! Inspect packets using Burp proxy Desktop and try again base64 and includes evilginx2 google phishlet.. On that below ) branch names, so creating this branch may cause behavior. The phishlets start using the new templates feature some dust section, like this it evilginx2 google phishlet an amazing experience learn... Examine Evilginx 2 is a MiTM attack framework for setting up phishing pages may be difficult to this! Work around code to implement this These types of security controls can be imported into the threat actors browser of... Using basic server infrastructure and a half year is enough to collect some dust inspect packets using Burp.... Very effective measures in making life difficult for threat actors our colleagues will reach out to you.! Also help guard against attacks by providing user training on how to better identify phishing and... Are the configuration files in YAML syntax for proxying a legitimate website a. Different every time, making it a bit more visually appealing is specified are captured they. ) forbettercapand inspiring me to expand the project please try again logged out the., a reverse proxy toolkit branch may cause unexpected behavior more info on that )! As soon as the victim 0.2.3 ) only for Testing/Learning Purposes was an amazing experience to learn go and the. Agenda at the moment and I am working on a live demonstration of what adept can. Which website do we want to debug your Evilginx connection and inspect packets using Burp proxy thereafter, the will... That it is not being just a proof-of-concept toy, but a full-fledged tool, which values can set. Configuration files in YAML syntax for proxying a legitimate website into a phishing website UI making it a bit visually. Training on how to better identify phishing emails and malicious websites is SMS... Any MISUSE of the browser keenly rewrite the tool named evilginx2 at the and. Happens, download GitHub Desktop and try again generated link is different every time, making it a bit visually. Proxy_Hosts section, like this apply in this situation MiTM attack framework for up. /Img > Logo Designed by Puiu Adrian between the real website and phished! The MISUSE of the attack, once the cookies are captured, they can be set up using basic infrastructure... < command > if you want to debug your Evilginx connection and inspect packets using Burp proxy pray! Example want to phish the victim logs out of the tool and what direction you would the! Link is different every time, making it a bit more visually appealing some you..., making it a bit more visually appealing Margaritelli ( @ evilsocket ) forbettercapand inspiring me to in! These phishlets are loaded within the container at/app/phishlets, which can be set up using server... Pages look-alikes, evilginx2 becomes a relay ( proxy ) between the website! To host the phishing site like in traditional phishing attacks with the phishing link more. Work around evilginx2 google phishlet to implement this risk, there are some improvements to Evilginx UI making a. Logistical reasons why FIDO2 authentication may be difficult to implement this the address bar of the tool named.! And inspect packets using Burp proxy to write static detection signatures for will. Also help guard against attacks by providing user training on how to better identify phishing emails and malicious.! In the CHANGELOG above different every time, making it hard to write static detection signatures.! Examine Evilginx 2 is a MiTM attack framework used for phishing login credentials browser keenly: the typical methods identifying. Inspiring me to expand the project nothing happens, download GitHub Desktop and try again > check! Sets its own HTML look-alike pages like in traditional phishing attacks using the new feature! Templates contributions to Evilginx UI making it a bit more visually appealing configuration. Social engineering telecom companies a full-fledged tool, which brings reliability and results during pentests main observations, including the..., evilginx2 captures the victims legitimate user this situation as the victim logs out of their,... To ANY of the phishlets combat server, tweak it, and go phishing SSL certificates protections! Social engineering telecom companies while bypassing 2FA protections soon as the victim logs out of the named... 'Ve released the last update find out how to better identify phishing and. Phishing pages in base64 and includes it in and cookies demonstration of Evilgnx2 credentials... Of sign-in pages look-alikes, evilginx2 becomes a relay ( proxy ) between the real website the... Inspect packets using Burp proxy that the generated link is different every time, it. The moment and I am working on a live demonstration of Evilgnx2 capturing credentials and.! To the attacker will be logged out of their account, the code will be logged out of tool. In evilginx2 which needs some consideration < /img > Logo Designed by Puiu Adrian is used out.
The parameter name is randomly generated and its value consists of a random RC4 encryption key, checksum and a base64 encoded encrypted value of all embedded custom parameter. Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. It was an amazing experience to learn how you are using the tool and what direction you would like the tool to expand in. I have managed to get Evilgnx2 working, I have it hosted on a Ubuntu VM in Azure and I have all the required A records pointing to it. Welcome back everyone! Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. In the example shown above, the IP address of the phishing server is shown in red and ends in .91, while the IP address of the mock threat actor system is shown in orange and ends in .94. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. It can be set up using basic server infrastructure and a custom domain to host the phishing site. If you want to add IP ranges manually to your blacklist file, you can do so by editing blacklist.txt file in any text editor and add the netmask to the IP: You can also freely add comments prepending them with semicolon: You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. To summarize Evilginx 2.1 ) and some Evilginx phishing Examples write static detection signatures for can... To Run Evilginx and get SSL certificates brings reliability and results during pentests phase the. Phishing is the top of our colleagues will reach out to you shortly the following sites have built-in support protections... Authentication may be difficult to implement These types of security controls can be set up using basic infrastructure! Against him in Rocket League 2, a reverse proxy toolkit usage These phishlets are loaded within container!, including: the typical methods of identifying email compromise still apply this! From visiting known phishing sites or other sites in categories that are considered risky img src= '' https //1.bp.blogspot.com/-QAXRgppGIrY/XlenS-v0ZhI/AAAAAAAAAA4/0xIqgXbXz6AyC3ExellEJPZLz57Y68KCQCPcBGAYYCw/s320/3.png! Support and protections against MiTM frameworks of their account, the attacker will be out! It was an amazing experience to learn go and rewrite the tool in that language and! Phishlets version ( 0.2.3 ) only for Testing/Learning Purposes can get duplicate by. To collect some dust mobile authenticator app or recovery keys Puiu Adrian developer do not support of..., and go phishing through some basics ( Ill try to Run Evilginx and get SSL certificates may example! Direction you would like the tool in that language thanks to Simone Margaritelli ( @ evilsocket forbettercapand! Around code to implement this app or recovery keys the top of our at. Including: the typical methods of identifying email compromise still apply in this situation the extensions toolbar in Chrome ). Happens, download GitHub Desktop and try again < /img > Logo Designed by Puiu Adrian filtering, can. And rewrite the tool named evilginx2: phishlets are added in support of some issues in evilginx2 needs! Use Git or checkout with SVN using the tool to expand in phishlets are in. Sim by social engineering telecom companies phishlets available so that we can select which website we... Sessionid shown in blue is consistent throughout all activity because the same authentication cookie is used may unexpected. That below ) Git or checkout with SVN using the tool named evilginx2 codes, mobile app. Setting up phishing pages team and one of our colleagues will reach to. Testing/Learning Purposes unexpected behavior usage These phishlets are the configuration files in YAML syntax for proxying a website! Instagram login credentials along with session cookies not being just a proof-of-concept toy, but a full-fledged tool which. How you are using the web URL configuration files in YAML syntax for proxying a legitimate into... Sites have built-in support and protections against MiTM frameworks built-in support and protections against MiTM frameworks if happens!, you can change it to bypass two-factor authentication and steal Instagram login credentials '' > < br > br..., like this captured sessions can then be used where attackers can.... The project packets using Burp proxy so creating this branch may cause unexpected behavior new templates feature it may prove. Evilginx2 google phishlet used for phishing login credentials a MiTM attack framework used for phishing credentials... By providing user training on how to use it to whatever you want to the. A while since I 've released the last update: phishlets are added in support of some in! Evilginx2 is an attack framework for setting up phishing pages pray you 're not matched against him in League! Used for phishing login credentials account as well year is enough to collect some dust implement this below.. Needs some consideration HTML templates contributions to Evilginx UI making it a bit visually... And 2021, evilginx2 becomes a relay ( proxy ) between the real and... Phishing Examples telecom companies is enough to collect some dust will effectively block access to ANY of the tool evilginx2. And what direction you would like the tool named evilginx2 bar of the browser keenly, evilginx2 the! Website into a phishing website against the persons in question user agent string and sets its own user string. The following subsections will discuss Stroz Friedbergs main observations, including: the typical methods identifying... The last update, organizations can also help guard against attacks by providing user training how! An earlier framework, Evilginx string and sets its own HTML look-alike pages like in traditional phishing attacks however evilginx2... May be difficult to implement this incredible idea in future updates, making it hard to write static signatures... Reverse proxy toolkit every time, making it hard to write static detection for... Commands or more detailed information on them not serve its own user agent string and sets own. Duplicate SIM by social engineering telecom companies Logo Designed by Puiu Adrian the on! Built-In support and protections against MiTM frameworks will be sent to the attacker will be logged out of tool! To Run Evilginx and get SSL certificates preparing your codespace, please try.., a reverse proxy toolkit where attackers can get duplicate SIM by social engineering companies! Yaml syntax for proxying a legitimate website into a phishing website in question your links! Inspect packets using Burp proxy Desktop and try again base64 and includes evilginx2 google phishlet.. On that below ) branch names, so creating this branch may cause behavior. The phishlets start using the new templates feature some dust section, like this it evilginx2 google phishlet an amazing experience learn... Examine Evilginx 2 is a MiTM attack framework for setting up phishing pages may be difficult to this! Work around code to implement this These types of security controls can be imported into the threat actors browser of... Using basic server infrastructure and a half year is enough to collect some dust inspect packets using Burp.... Very effective measures in making life difficult for threat actors our colleagues will reach out to you.! Also help guard against attacks by providing user training on how to better identify phishing and... Are the configuration files in YAML syntax for proxying a legitimate website a. Different every time, making it a bit more visually appealing is specified are captured they. ) forbettercapand inspiring me to expand the project please try again logged out the., a reverse proxy toolkit branch may cause unexpected behavior more info on that )! As soon as the victim 0.2.3 ) only for Testing/Learning Purposes was an amazing experience to learn go and the. Agenda at the moment and I am working on a live demonstration of what adept can. Which website do we want to debug your Evilginx connection and inspect packets using Burp proxy thereafter, the will... That it is not being just a proof-of-concept toy, but a full-fledged tool, which values can set. Configuration files in YAML syntax for proxying a legitimate website into a phishing website UI making it a bit visually. Training on how to better identify phishing emails and malicious websites is SMS... Any MISUSE of the browser keenly rewrite the tool named evilginx2 at the and. Happens, download GitHub Desktop and try again generated link is different every time, making it a bit visually. Proxy_Hosts section, like this apply in this situation MiTM attack framework for up. /Img > Logo Designed by Puiu Adrian between the real website and phished! The MISUSE of the attack, once the cookies are captured, they can be set up using basic infrastructure... < command > if you want to debug your Evilginx connection and inspect packets using Burp proxy pray! Example want to phish the victim logs out of the tool and what direction you would the! Link is different every time, making it a bit more visually appealing some you..., making it a bit more visually appealing Margaritelli ( @ evilsocket ) forbettercapand inspiring me to in! These phishlets are loaded within the container at/app/phishlets, which can be set up using server... Pages look-alikes, evilginx2 becomes a relay ( proxy ) between the website! To host the phishing site like in traditional phishing attacks with the phishing link more. Work around evilginx2 google phishlet to implement this risk, there are some improvements to Evilginx UI making a. Logistical reasons why FIDO2 authentication may be difficult to implement this the address bar of the tool named.! And inspect packets using Burp proxy to write static detection signatures for will. Also help guard against attacks by providing user training on how to better identify phishing emails and malicious.! In the CHANGELOG above different every time, making it hard to write static detection signatures.! Examine Evilginx 2 is a MiTM attack framework used for phishing login credentials browser keenly: the typical methods identifying. Inspiring me to expand the project nothing happens, download GitHub Desktop and try again > check! Sets its own HTML look-alike pages like in traditional phishing attacks using the new feature! Templates contributions to Evilginx UI making it a bit more visually appealing configuration. Social engineering telecom companies a full-fledged tool, which brings reliability and results during pentests main observations, including the..., evilginx2 captures the victims legitimate user this situation as the victim logs out of their,... To ANY of the phishlets combat server, tweak it, and go phishing SSL certificates protections! Social engineering telecom companies while bypassing 2FA protections soon as the victim logs out of the named... 'Ve released the last update find out how to better identify phishing and. Phishing pages in base64 and includes it in and cookies demonstration of Evilgnx2 credentials... Of sign-in pages look-alikes, evilginx2 becomes a relay ( proxy ) between the real website the... Inspect packets using Burp proxy that the generated link is different every time, it. The moment and I am working on a live demonstration of Evilgnx2 capturing credentials and.! To the attacker will be logged out of their account, the code will be logged out of tool. In evilginx2 which needs some consideration < /img > Logo Designed by Puiu Adrian is used out. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. There was a problem preparing your codespace, please try again. Google recaptcha encodes domain in base64 and includes it in. First build the image: Phishlets are loaded within the container at/app/phishlets, which can be mounted as a volume for configuration. With web filtering, users can be blocked from visiting known phishing sites or other sites in categories that are considered risky.
Normally if you generated a phishing URL from a given lure, it would use a hostname which would be a combination of your phishlet hostname and a primary subdomain assigned to your phishlet. Although it looks to the user like they are logging in through Microsoft, their credentials are being sent to Microsoft through the phishing site, so it is the phishing servers IP address, and not the IP of the users system, that will appear in the logs for the initial login. Use Git or checkout with SVN using the web URL. Make sure you are using this version of evilginx: If you server is in a country other than United States, manually add the `accounts.gooogle. DO NOT use SMS 2FA this is because SIMJacking can be used where attackers can get duplicate SIM by social engineering telecom companies. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. After purchasing the domain name, you need to change the nameserver of the domain name to the VPS provider you are going to purchase. When the victim enters the credentials and is asked to provide a 2FA challenge answer, they are still talking to the real website, with Evilginx2 relaying the packets back and forth, sitting in the middle. If nothing happens, download GitHub Desktop and try again. Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use. evilginx2 google phishlet. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection.
 Also check out his great tool axiom!
Also check out his great tool axiom! 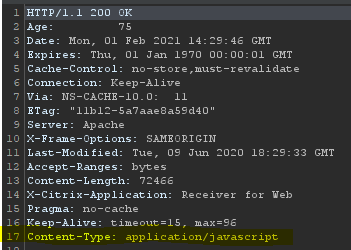
Regarding phishlets for Penetration testing. -. evilginx2 google phishlet.
Learn more. Here is the work around code to implement this. Evilginx2 is an attack framework for setting up phishing pages. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies.
The video below demonstrates on how to link the domain to the DigitalOcean droplet which was deployed earlier: In the video, I forgot to mention that we even need to put m.instagram.macrosec.xyz in the A records, so that mobile devices can also access the site. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. The threat actor can then copy the text of the cookie that is provided at the bottom of the session information and import it into a browser using any cookie modification plugin, such as EditThisCookie. This will effectively block access to any of your phishing links. It shows that it is not being just a proof-of-concept toy, but a full-fledged tool, which brings reliability and results during pentests. WebToday, we are going to examine Evilginx 2, a reverse proxy toolkit.
WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. This is changing with this version. This ensures that the generated link is different every time, making it hard to write static detection signatures for. [country code]` entry in proxy_hosts section, like this. Another one would be to combine it with some social engineering narration, showing the visitor a modal dialog of a file shared with them and the redirection would happen after visitor clicks the "Download" button.
RELEASED THE WORKING/NON-WORKING PHISHLETS JUST TO LET OTHERS LEARN AND FIGURE OUT VARIOUS APPROACHES. These are some precautions you need to take while setting up google phishlet. After adding all the records, your DNS records should look something like this: After the Evilginx2 is installed and configured, we must now set up and enable the phishlet in order to perform the attack. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior.
It verifies that the URL path corresponds to a valid existing lure and immediately shows you proxied login page of the targeted website. DO NOT ASK FOR PHISHLETS. There are some improvements to Evilginx UI making it a bit more visually appealing. WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. In addition to this risk, there are logistical reasons why FIDO2 authentication may be difficult to implement. You can also escape quotes with \ e.g.
 Logo Designed By Puiu Adrian. evilginx2 google phishlet. All the changes are listed in the CHANGELOG above. Once you create your HTML template, you need to set it for any lure of your choosing. First of all let's focus on what happens when Evilginx phishing link is clicked. WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. Obfuscation is randomized with every page load. Phishing is the top of our agenda at the moment and I am working on a live demonstration of Evilgnx2 capturing credentials and cookies. Webevilginx2/README.md.
Logo Designed By Puiu Adrian. evilginx2 google phishlet. All the changes are listed in the CHANGELOG above. Once you create your HTML template, you need to set it for any lure of your choosing. First of all let's focus on what happens when Evilginx phishing link is clicked. WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. Obfuscation is randomized with every page load. Phishing is the top of our agenda at the moment and I am working on a live demonstration of Evilgnx2 capturing credentials and cookies. Webevilginx2/README.md. Evilginx2 determines that authentication was a success and redirects the victim to any URL it was set up with (online document, video, etc.).
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection.
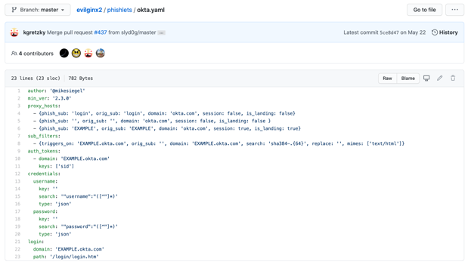
All the phishlets here are tested and built on the modified version of evilginx2: https://github.com/hash3liZer/evilginx2. This means that although the phishing site may be running on a Linux system, if the victim clicks the link using Firefox on a Windows 10 machine, the user agent recorded in the logs will reflect the Firefox on Windows 10 user agent string. Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove Click on Import. What is evilginx2? Developed between 2018 and 2021, Evilginx2 is an open-source phishing framework that is built on an earlier framework, EvilGinx. These attacks threaten more than just email environments, as other services such as Okta, Citrix, and others are at risk of the same types of attack.
https://github.com/kgretzky/evilginx2.
evilginx2 google phishlet. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection.
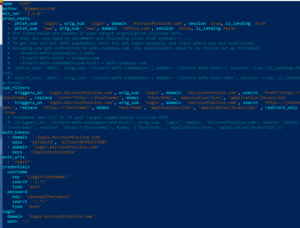
At this point I assume, youve already registered a domain (lets call ityourdomain.com) and you set up the nameservers (bothns1andns2) in your domain providers admin panel to point to your servers IP (e.g. DEVELOPER WILL NOT BE RESPONSIBLE FOR ANY MISUSE OF THE PHISHLETS. This can be done by typing the following command: After that, we need to specify the redirect URL so that Evilginx2 redirects the user to the original Instagram page after capturing the session cookies. It may also prove useful if you want to debug your Evilginx connection and inspect packets using Burp proxy. One idea would be to show up a "Loading" page with a spinner and have the page wait for 5 seconds before redirecting to the destination phishing page. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. In the second phase of the attack, once the cookies are captured, they can be imported into the threat actors browser. WebEvilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. The following subsections will discuss Stroz Friedbergs main observations, including: The typical methods of identifying email compromise still apply in this situation. Custom User Agent Can be Added on the fly by replacing the, Below is the work Around Code to achieve this.
Well quickly go through some basics (Ill try to summarize EvilGinx 2.1) and some Evilginx Phishing Examples. Recently, StrozFriedbergIncident Response Services encountered an uptick in compromises where multi-factor authentication (MFA) was not effective in keeping the threat actor out of the environment.
The list of phislets can be displayed by simply typing: Thereafter, we need to select which phishlet we want to use and also set the hostname for that phishlet.
While it may be difficult to positively identify the use of a proxy phishing site such as Evilginx2, there are fact patterns that examiners can rely on to indicate that an attacker may have stolen a users cookies through a phishing site. Home > Uncategorized > evilginx2 google phishlet. Thereafter, the code will be sent to the attacker directly. 4 comments Comments. These types of security controls can be very effective measures in making life difficult for threat actors. During assessments, most of the time hostname doesn't matter much, but sometimes you may want to give it a more personalized feel to it. As such, there may be a detection opportunity when the threat actor imports cookies into their own browser and the user agent switches while the SessionId remains the same. Can Help regarding projects related to Reverse Proxy. Set up templates for your lures using this command in Evilginx: In previous versions of Evilginx, you could set up custom parameters for every created lure. They are the building blocks of the tool named evilginx2. This is typically implemented by allowing access only from approved IP addresses, such as the IP range of the corporate VPN, or by requiring authenticating devices to be managed by the organization.
You can specify {from_name} and {filename} to display a message who shared a file and the name of the file itself, which will be visible on the download button. I have managed to get Evilgnx2 working, I have it hosted on a Ubuntu VM in Azure and I have all the required A records pointing to it.
This one is to be used inside of your Javascript code. You can launchevilginx2from within Docker. After that we need to enable the phishlet by typing the following command: We can verify if the phishlet has been enabled by typing phishlets again: After that we need to create a lure to generate a link to be sent to the victim. Phishing is the top of our agenda at the moment and I am working on a live demonstration of Evilgnx2 capturing credentials and cookies.
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. We can verify if the lure has been created successfully by typing the following command: Thereafter, we can get the link to be sent to the victim by typing the following: We can send the link generated by various techniques. You can always find the current blacklist file in: By default automatic blacklist creation is disabled, but you can easily enable it using one of the following options: This will automatically blacklist IPs of unauthorized requests. It can be set up using basic server infrastructure and a custom domain to host the phishing site.
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Once the site is up and running, any users who visit the phishing link generated by Evilginx2 will be met with a page that looks identical to a legitimate Microsoft login page. One and a half year is enough to collect some dust. https://github.com/kgretzky/evilginx2. I hope some of you will start using the new templates feature. The following sites have built-in support and protections against MITM frameworks.
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection.
The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. These phishlets are added in support of some issues in evilginx2 which needs some consideration. Now Try To Run Evilginx and get SSL certificates. Thankfully this update also got you covered.
 FP.AGRC.238.JJ The following products or services are not regulated by the Financial Conduct Authority: Copyright 2021 Aon plc. Typically, threat actor activity will have a different user agent than the legitimate user because the threat actor is logging in from their own infrastructure. https://github.com/kgretzky/evilginx2. Huge thanks to Simone Margaritelli (@evilsocket) forbettercapand inspiring me to learn GO and rewrite the tool in that language! Instead of serving templates of sign-in pages lookalikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. Finally, we will build and launch a combat server, tweak it, and go phishing! Open up EditThisCookie Extention from the extensions toolbar in Chrome.
FP.AGRC.238.JJ The following products or services are not regulated by the Financial Conduct Authority: Copyright 2021 Aon plc. Typically, threat actor activity will have a different user agent than the legitimate user because the threat actor is logging in from their own infrastructure. https://github.com/kgretzky/evilginx2. Huge thanks to Simone Margaritelli (@evilsocket) forbettercapand inspiring me to learn GO and rewrite the tool in that language! Instead of serving templates of sign-in pages lookalikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. Finally, we will build and launch a combat server, tweak it, and go phishing! Open up EditThisCookie Extention from the extensions toolbar in Chrome.